http://www.slideshare.net/cavsa01/ibm-swg-security-portfolio-20140731
Ibm swg security portfolio 20140731
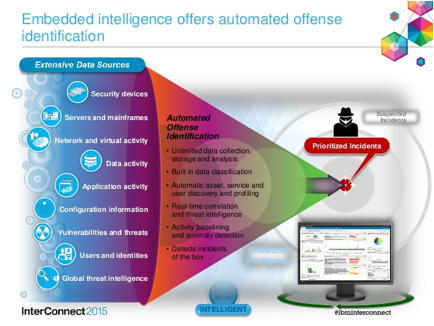
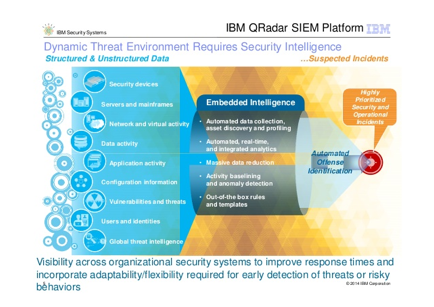
automated offense identification
- See more at:
in-depth forensics data incidents
- See more at:
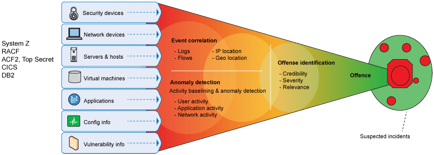
http://www.slideshare.net/ibmsecurity/security-intelligence-big-data-advanced-analytics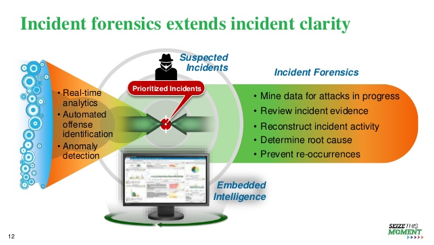
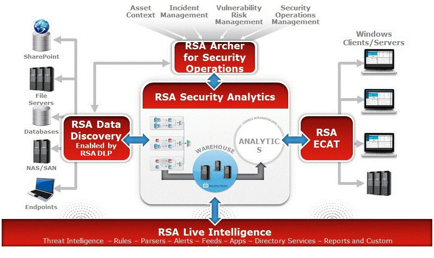
- See more at:
http://www.datawebsecurity.co.uk
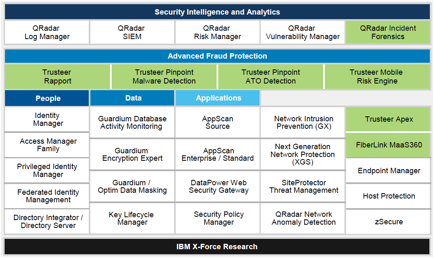
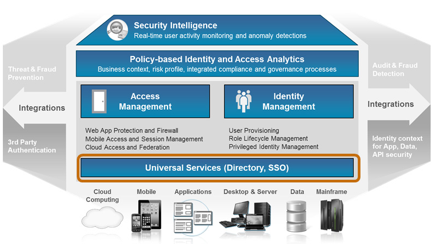
evolving the ibm security
intelligence strategy based client
-
See more at:
http://www.ibm.com/developerworks/library/se-directoryintergrator72/
IBM Security Directory Integrator 7.2:
Completing the security perimeter
The former Tivoli
Directory Integrator provides real-time synchronization between identity data
sources
20 January 2014
-
See more at:
https://turbotodd.wordpress.com/2011/09/30/ibm-x-force-trends-report-year-of-the-security-breach/
IBM X-Force Trends Report: Year Of The Security Breach
- See more at:
http://www.slideshare.net/ibmcanada/ibm-canada-strategic-cloud-security

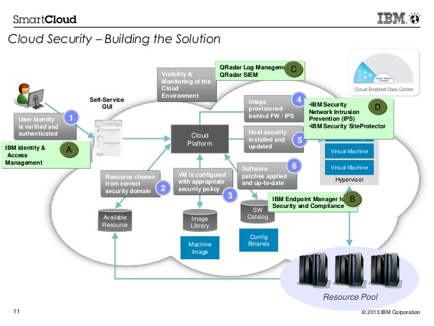
ibm security intelligence
http://www.slideshare.net/IBMDK/ibm-security-and-strategy-v-fabio-panada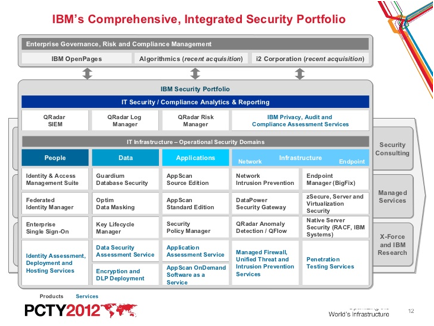
ibm security unified architecture web-based console
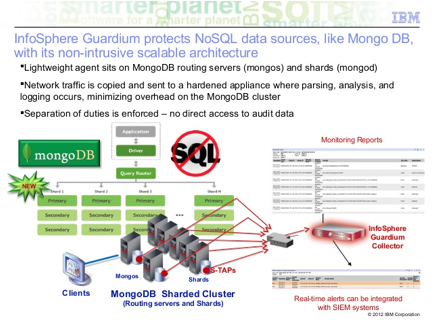
http://www.slideshare.net/cavsa01/guardium-91-overview-2014
IBM InfoSphere Guardium
9.1 overview 2014
http://expertintegratedsystemsblog.com/2013/10/oct8_screadynow_announcement_benelux/
IT Infrastructure Matters:
IBM PureSystems October 8 Announcement Recap
October 17, 2013 3:48 am by
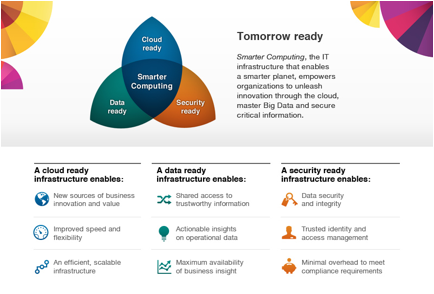
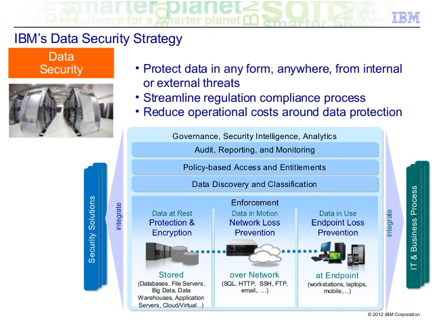
http://www.slideshare.net/ibmdatapower/data-power-common-use-cases
Published on May 09, 2013
IBM DataPower Gateway
appliances are used in a variety of user scenarios to enable security,
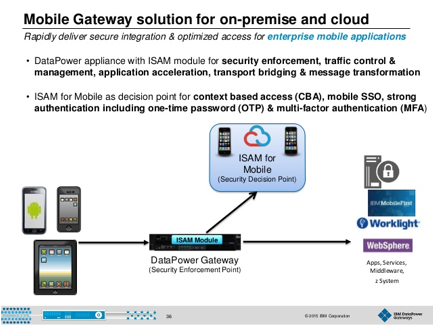
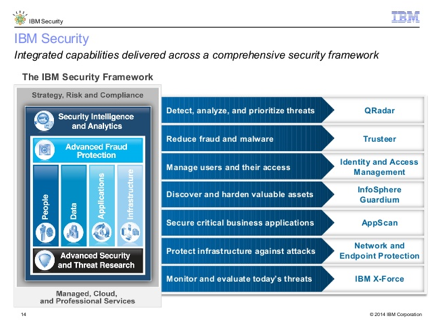
ibm security delivering
multiple security capabilities
Dispatches from the front:
What does it take to deploy IBM Security QRadar?
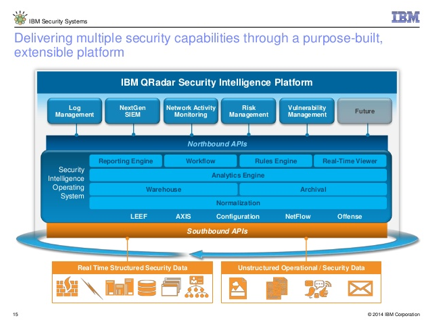
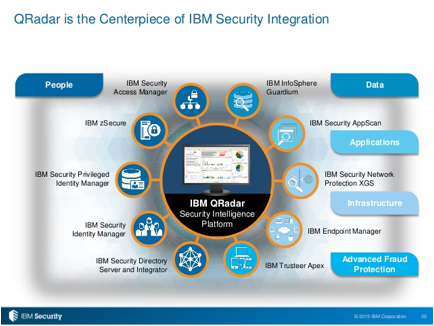
ibm qradar centerpiece security integration
ibm x-force exchange
ibm bigfix protect your data endpoints
ibm bigfix protect your data endpoints always-on security
ibm bigfix policy driven endpoint manager
ibm bigfix patch management single intelligent agent
ibm bigfix inventory software usage single intelligent agent
ibm bigfix :lifecycle mgmt, core protection, inventory software usage, patch mgmt
mobilefirst protect, security and compliance
ibm security bigfix architecture how it work
Big Fix Architectural
Overview
http://www.slideshare.net/bdhaus1/big-fix-architectural-overview
http://www-03.ibm.com/security/bigfix/
ibm maas360 solution overview
http://content.maas360.com/www/content/sb/sb_maas360_mdm_IBM_Security_Solutions.pdf
http://content.maas360.com/www/content/ds/ds_FiberlinkCompanyOverview.pdf
ibm maas360 top mobility initiatives solution overview
ibm maas360 top mobility initiatives solution overview protect sensitive corp data
ibm maas360 mobile enterprise gateway sap afaria
ibm maas360 mobile enterprise gateway
ibm maas360 enterprise mobility management
ibm security appscan v9 overview
ibm app security trends affecting cust
appscan impacts app vulnerabilities enormous
ibm appscan application security management
ibm appscan application security risk management
ibm appscan application security framework
ibm application security delivery framework
test app in development
dynamic analysis
http://www-03.ibm.com/software/products/en/appscan-dynamic-analyzer
IBM Security
AppScan¨ Dynamic Analyzer is designed to help secure your organizationÕs web
applications deployed on IBM BluemixĒ by detecting dozens of todayÕs most
pervasive published security vulnerabilities. It provides a progressive,
self-controlled web application security approach available for trial and
purchase from IBM Bluemix.
As part of
the application development lifecycle, IBM Security AppScan Dynamic Analyzer
helps eliminate security vulnerabilities from web applications before they are
placed into production and deployed. It provides convenient application
scanning without requiring significant training or advance preparation.
IBM Security
AppScan Dynamic Analyzer:
Scans web applications that are deployed on IBM
Bluemix at the
appropriate stage of your development lifecycle.
Identifies security vulnerabilities at the application level.
Delivers a detailed report that explains the vulnerability, your
potential risk and best practices to remediate it.
static analysis
interactive analysis
mobile application analysis
https://www.owasp.org/images/c/c9/Mobile-threat-analysis-short-presentation_owasp.pdf
Mobile App Threat Analysis - Ari Kesaniemi Nixu
http://www.ibm.com/developerworks/library/se-test-mobile-security-appscan/index.html
Streamline your organization's mobile
application security testing program with IBM Security AppScan Source 9.0
Identify and correct
vulnerabilities Jun
2014
Mobile apps are developed and delivered at a fast pace. The
148Apps.biz website (see Resources) reports that over a
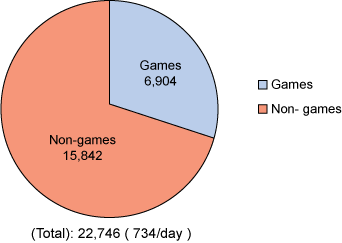
million active apps were added to the iTunes App Store since 2008. As shown in
Figure 1, nearly 7,000 game apps were submitted in March 2014 alone, along with
more than 15,000 non-game apps.
Figure
1. iTunes App store submission numbers for March 2014
While these apps bring convenience and enjoyment to users, are
they secure and protected from hackers?
The research of IBM Business Partner Arxan determined that among
the top 100 paid applications:
¯
100% of apps on the Google Android platform were hacked.
¯
56% of apps on Apple iOS were hacked.
Among the popular free applications:
¯
73% on Android were hacked.
¯
53% on Apple iOS were hacked.
See
Resources for a link to ArxanÕs reports.
http://www-03.ibm.com/software/products/en/appscan-mobile-analyzer
IBM Security AppScan
Mobile Analyzer
IBM Security
AppScan Mobile Analyzer:
o
Scans mobile
applications at the
appropriate stage of your development lifecycle.
o
Identifies
security vulnerabilities to malware
and other security threats.
o
Delivers a
detailed report that
explains the vulnerability, your potential risk and best practices to remediate
it.
Scans mobile applications
o
Uses IBM
mobile interactive application security testing (IAST) technology.
o
Provides an
intuitive user interface.
o
Explores applications
to discover elements that should be tested.
o
Analyzes
manifest files and dynamically learns of intent parameters.
o
Sends intents
with malicious payloads using security knowledge.
Identifies security vulnerabilities
o
Sends intents
with malicious payloads using IBM Security knowledge.
o
Simulates
attacks to trigger vulnerabilities.
o
Places hooks
on target mobile applications.
o
Detects many
types of issues, including: Cross-Application Scripting (XAS), Insecure Pending
Intent, UI Spoofing, Insecure File Rights and more.
Delivers a detailed report
o
Provides an
executive summary, isolates critical issues and offers recommendations for
remediation.
o
Includes
function, class and line information to expedite remediation.
o
Delivers
ratings for vulnerabilities to support prioritization and developer
productivity.
o
Formulates an
action plan for remediation of vulnerabilities.
o
Permits you
to rescan your application to verify that issues have been remediated.
static analysis security test
http://www.ibm.com/developerworks/library/se-testing/
Secure your mobile applications
Find vulnerabilities with
IBM Security AppScan Standard
With the explosive
growth in the mobile ecosystem, mobile application security is a huge concern.
New mobile application designs require new ways of testing to ensure data
safety. In this article, explore different aspects of mobile application
security. With hands-on examples, learn to use IBM¨ Security AppScan¨ Standard
with mobile user agents and with emulators and actual devices for Android and
iOS.
. . .
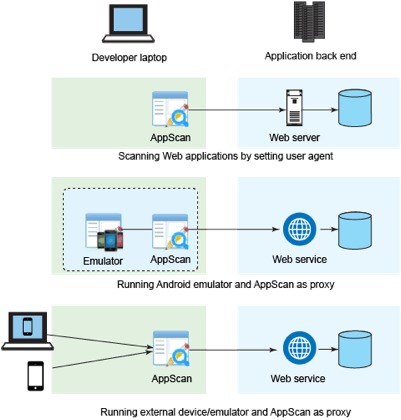
using IBM Security AppScan Standard Edition. Learn to set up
AppScan to scan mobile applications with three different models:
Scanning mobile web
applications by setting up a mobile user agent
Using an emulator for
both iOS and Android
Configuring an actual
mobile device for both Android and iOS
Figure 1 shows the three different configurations.
Figure
1. Methods to scan and test mobile applications
isam for web
http://www-03.ibm.com/software/products/no/access-mgr
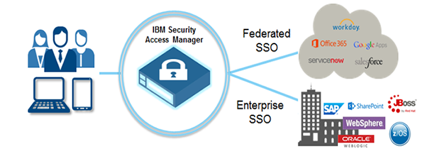
IBM Security
Access Manager integrated appliance is designed to:
Manage Access in the world of Hybrid Cloud: Enable SSO and identity federation to apps
running inside & outside of the enterprise.
Provide risk-aware access security for mobile
apps and APIs:
Transparently register mobile devices and enforce user-centric authentication
policies.
Remove barriers to mobile productivity: Enable more convenient and secure access to
enterprise resources from mobile.
Manage Access
in the world of Hybrid Cloud
v Quickly establish single sign-on connections to
popular SaaS applications
v More easily create custom application
connectors with Do-It-Yourself federations based on SAML 2.0 standard
v Deliver single sign-on to enterprise
applications and support user identity propagation in hybrid cloud application
interactions
v Simplified deployment and management with
appliance-based packaging is suitable for small-to-medium size businesses and
scalable for large enterprises
Provide
risk-aware access security for mobile apps and APIs

v Dynamically assess risk associated with mobile
app access using contextual information about the device, user, environment,
resource, malware, device management status and past user behavior
v Strong and multi-factor authentication
capabilities protect critical sensitive assets depending on the risk context
v Audit or block fraudulent and high-risk
transactions from infected devices without modifying backend applications
Remove
barriers to mobile productivity
v Allows users to easily access enterprise
resources with minimal authentication friction
v Utilizes existing access management
infrastructure to prevent the need for application changes while enabling
access from mobile devices
v Enhance productivity and user experience with
device-level single sign-on to enterprise resources from MobileFirst Protect
managed devices
isam for mobile
http://www.ibm.com/developerworks/library/se-mobile/
Introducing IBM Security Access Manager for
Mobile
Discover how ISAM for
Mobile helps you secure mobile user access and manage mobile app security jan 2014
The highly scalable and configurable IBM Security Access Manager
for Mobile delivers mobile access security protection in a modular virtual or
physical hardware appliance package, enabling you to quickly and securely
manage both mobile user access and applications while helping you safeguard
mobile, cloud, and social interactions across the enterprise.
In this demonstration, you'll see how ISAM for Mobile helps you:
o Initiate mobile single sign-on and sessions
management to provide secure access to mobile and web applications.
o Enable context-aware authorization using
device fingerprinting, geolocation awareness, and IP reputation mechanisms.
o Provide integrated identity assurance
authentication schemes such as one-time password (OTP; a password that is valid
for only one login session or transaction) and RSA SecurID token support (a
mechanism for performing two-factor authentication for a user to a network
resource).
o
Deliver compliance and security intelligence—the
combination of advanced analytics, expert analysis, and swift
remediation—through tight integration with IBM Security QRadar products.
ISAM for Mobile also integrates well with IBM Worklight, an
advanced development platform for designing, developing, and deploying native,
web, and hybrid mobile applications.
The demonstration highlights several scenarios you're likely to
encounter while delivering mobile security access services:
¯
Risk-based access. Watch and learn how the software compares
current device fingerprints against previously registered user fingerprints.
¯
Simulated mobile phone application. Examine how to create
and implement an enforced policy that allows a transaction for less than US$100
to automatically go through, requests more authentication if the transaction is
more than US$100, and denies the transaction if it is greater than US$1000.
¯ Building policy rules. See how to define and
create unconditional and conditional rules for access policy. (Unconditional
rules have three options: Allow, deny, request more information. Conditional
rules let you define more parameters before the access decision is made,
including such parameters as geolocation, IP reputation exclusion, and so on.)
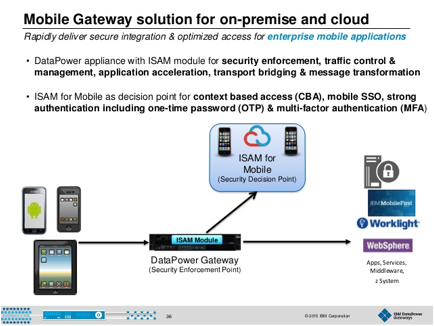
ibm security access manager family identity manager
ibm security access manager family identity manager access manager web mobile cloud
ibm federated identity manager
http://www.ibm.com/developerworks/websphere/library/techarticles/1208_rasmussen/1208_rasmussen.html
Implementing OAuth on IBM WebSphere DataPower
Appliances, Part 1: Introducing OAuth 2.0 support in DataPower
This article is the
first in a multi-part series of articles describing OAuth support on WebSphere¨
DataPower Appliances. Part 1 starts with an overview of OAuth and then
describes DataPower support for OAuth roles. The rest of the article series
will go into detail on several aspects of OAuth and DataPower usage and
configuration.
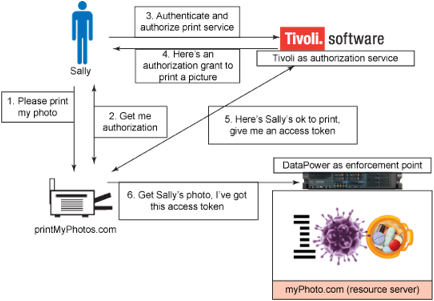
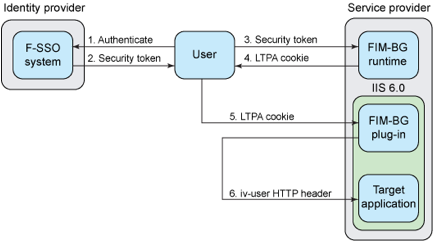
http://www.networkworld.com/article/2285444/tech-primers/understanding-federated-identity.html
Understanding federated identity
By William Stallings, special to
Network World
Network World | Aug 31, 2007 1:00 AM PT
The focus of identity management is defining an identity
for each user (human or process), associating attributes with the identity and
enforcing a means by which a user can verify identity. Once implemented,
identity-management systems support single sign-on (SSO), the ability of a user
to access all network resources after a single authentication.
The principal standard for federated
identity is the Security Assertion Markup Language (SAML), which defines the
exchange of security information between online business partners.
SAML is part of a broader collection of standards being
issued by the Organization for the Advancement of Structured Information
Standards for federated identity management. For example, WS-Federation enables
browser-based federation; it relies on a security token service to broker trust
of identities, attributes and authentication between participating Web
services.
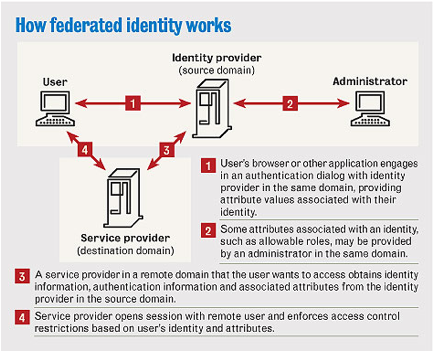
https://www-304.ibm.com/connections/blogs/sweeden/?maxresults=10&lang=en_us
What is IBM Bluemix?
Put simply, IBM Bluemix is a Platform-as-a-Service (PaaS) offering
from IBM. Based on CloudFoundry open source technology, IBM Bluemix allows
developers to rapidly assemble and deploy applications. What differentiates
IBM's PaaS offering is the wealth of value-add services from both IBM's
middleware stack and partners.
What is IBM Single Sign On for Bluemix?
The single sign on service for Bluemix allows a developer to add
authentication services to their application in less than an hour.
Actually, much less in most cases. How could that be?
The
single sign on service does this by providing zero-code (or minimum-code)
integration of single sign on into applications. A security administrator
creates a service instance, then configures one or more "identity
sources" for that service instance. A developer then binds that service
instance to their application. Specifically for J2EE applications that use the
Liberty Java application runtime on Bluemix, the act of binding the service
instance to the application results in completely automated configuration of
federated single sign on security between the original identity sources and the
target application.
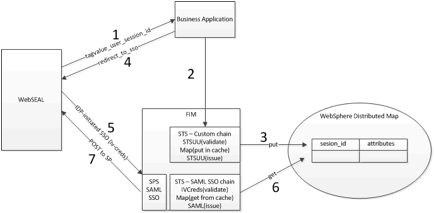
http://docs.oracle.com/cd/E28280_01/admin.1111/e13400/plandeploy.htm
- SFSAG731
Planning
Oracle Identity Federation Deployment
This chapter outlines Oracle Identity
Federation deployment considerations and helps you understand installation
options. It contains these sections:
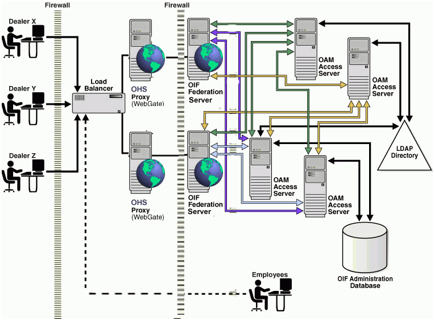
http://windowsitpro.com/active-directory/ease-cloud-security-concerns-federated-identity
Ease Cloud Security Concerns with Federated Identity
Securely extend Active DirectoryÕs reach into the cloud
Mar 9, 2011
Why We Need Federated Identity
To understand the growing
popularity of federated identity, it helps to look at the challenges that IT
professionals and developers face when using traditional identity
authentication in the modern IT environment—in particular, the Kerberos
protocol. The point behind an identity provider, such as Active Directory (AD), is
to centralize identity information for resources to consume. Although
identity-oriented IT pros tend to lose sight of it, the purpose of the
authentication process is to determine and validate the userÕs identity in
order to gain access to resources.
The Kerberos security protocol (and
therefore the AD domains and forests built on it) was designed to work in a
fairly secure environment, such as a corporate intranet. The Kerberos protocol,
as implemented in AD, provides two components: confirmation of identity and
security group membership. If a resource (e.g., a DFS namespace) requires more
information, such as site information, it needs to extract that information
from another location—AD itself.
However, scenarios that donÕt
require any modification of AD to store more information are pretty simplistic
in real life. Microsoft Exchange Server, for example, requires more information
about a user than the base AD schema provides. So, AD admins must extend the
schema to allow Exchange to store added identity data about its users. Schema
extensions arenÕt done casually; they take time to prepare for and schedule. As
a result, other applications might choose to store identity information in
databases such as SQL Server or Active Directory Lightweight Directory Services
(AD LDS) that donÕt require the amount of preparation a schema change does.
But what if the users and resources
are in two different enterprises—for example, a joint venture or
collaboration, or for a Software as a Service (SaaS) cloud application? Do you create and manage the external usersÕ identities by
creating shadow accounts in AD, or do your developers create a separate account
database to hold them? How do you keep up with the
accurate provisioning and deprovisioning of these accounts? What about
providing adequate security for these identities against hackers?
Most companies donÕt want to manage
external usersÕ identities and the headaches that go along with that
management. If an application is intended to support multiple access scenarios,
developers must build in multiple authentication mechanisms. Identity design
and management in these and other scenarios become very cumbersome, and the
traditional model is stretched to its limit.
What Federated Identity Is
The federated identity model can
handle a variety of scenarios. Federated identity is the ability to port data
across security domains using claims and assertions from a digitally signed
identity provider. To understand what that definition means, letÕs break it
into parts. As I described in the previous section, each enterpriseÕs
identity store can be generically described as a security domain,
regardless of whether itÕs using AD or some other directory product. For the
purpose of this article, AD is the identity provider for scenarios
inside an enterprise. For scenarios that span multiple enterprises, the
identity provider is the entire enterprise that provides identity information
(not just AD). As for claims and assertions, these are essential
parts of what we call claims-based authentication.
Claims-based authentication is the
cornerstone of federated identity. At its simplest, claims-based authentication
is about presenting an application with the potentially wide variety of identity
information it needs, from an identity provider it trusts, in a highly secure
envelope, regardless of whether the application is inside or outside the
enterprise. ThatÕs why it can handle the two-enterprise and SaaS scenarios that
I discussed in the previous section so well. Claims-based authentication adds
flexibility and security, whereas traditional authentication technology gives
you either flexibility (LDAP queries to AD) or security (Kerberos).
The claims-based authentication
model is based on a few simple, intuitive concepts, but the authentication
process can bounce back and forth quite a bit. LetÕs compare some of the basics
of this model with one you know a little better: the Kerberos protocol.
In AD, every authenticated user has
one or more Kerberos tickets that contain identity information. A basic
construct of claims-based authentication is the token, formatted in Security
Assertion Markup Language (SAML). Figure 1 shows an SAML token, which is
similar to a Kerberos ticket in many ways. A Kerberos ticket contains a
payload, called the access token, that asserts what security groups the user is
a member of. The resource (e.g., a file server) trusts this assertion, because
the ticket is cryptographically confirmed to be from a valid identity
source—which in AD is the Kerberos Key Distribution Center (KDC) of the
domain controller (DC) the file server is talking to.
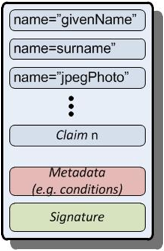
Figure 1: SAML token
An SAML token is in fact called an
assertion. The payload of this assertion contains a potentially far broader set
of identity information, called claims, than a Kerberos ticket holds. An SAML
token is designed to be much more flexible in this regard. A claim can be
anything you define it to be: name, email, phone number, age, privilege level,
meal preference, etc.
In AD, a Kerberos ticket has time
restrictions regarding when it can be used. This prevents replay attacks, in
which packets are captured then played back to a server at a later time in an
attempt to compromise it. An SAML assertion also contains conditions that place
more stringent restrictions on when the assertion is valid than the Kerberos
protocol is capable of doing. You can restrict when the assertion is valid, who
can use the assertion, how many times it can be used, and whether the assertion
can be delegated. Thus, an assertion can be highly targeted toward a specific
use, and that use only, to increase the security of the authentication process.
Finally, an AD Kerberos ticket is
encrypted with either the ticket-granting server key (for a ticket-granting
ticket—TGT) or the user key (for a session ticket). An SAML assertion is
signed and can have various degrees of encryption from the identity provider
that created it, from individual components to the entire assertion. The
signing ensures that the assertion is indeed from the stated identity provider
and hasn't been tampered with, and the encryption ensures that the assertion
hasnÕt been spied on.
For all these similarities, though,
hereÕs the most important distinction: The scope of an AD Kerberos ticket is
essentially within the enterprise, whereas an SAML token has no restrictions of
this kind at all. This means that a claims-aware application can authenticate
users equally comfortably inside or outside the corporate firewall.
This token doesnÕt appear out of
thin air. Something has to create it, and AD doesnÕt know anything about this
process. Enter yet another component of the claims world: the Security Token
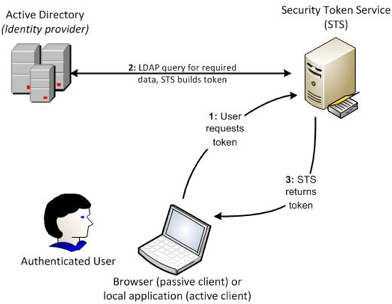
Service. The STS issues tokens on behalf of requests from users. Figure 2 shows
how an STS interacts with a user and AD to build a token that can be presented
to claims-aware applications. Note that Figure 2 explicitly shows the userÕs
browser. This is because it can be closely involved in the process if the
userÕs OS doesnÕt have a client that understands the token-passing process.
Figure 2: STS
token-creation process
How Federated Identity Works: Two
Scenarios
Now that IÕve introduced all the players
involved in claims-based authentication, letÕs take a look at how all these
components work together to authenticate a user to an application. ItÕs kind of
a complicated dance, but itÕs almost entirely transparent to the user. Because
of federationÕs flexibility, federated identity is used in several different
scenarios. In this article, I focus on just the two most likely scenarios
youÕll face. In these scenarios, you must first set up a federated trust
between your federation service and the service provider. This necessary step
lets the service providerÕs STS decrypt the encrypted claims coming from your
companyÕs federation service; it also lets your STS accept claims requests from
the service provider.
The first scenario occurs when a
user inside the enterprise attempts to access a claims-aware application thatÕs
also inside the enterprise. This situation might not exist in your organization
today, but it will be common in the near future as more applications become
claims aware and as the private cloud becomes more popular.
The process of an internal user
accessing an internal application includes many individual steps, as Figure 3
shows.
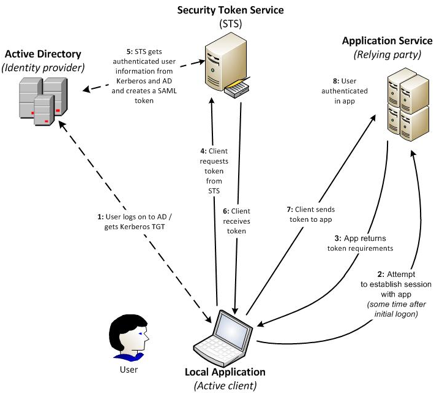
fig 3: internal user accessing an
internal application
However, this scenario is easier to
understand if you keep in mind the high-level process.
o
The application hits a point at
which it can no longer continue (e.g., it needs identity data for the user).
o
The application triggers or
initiates either a web service call (if the client is active and has some way of
understanding the call) or an HTTP redirect through the browser (if the client
is passive and canÕt handle such a request) to ask for a token from an STS.
o
The STS responds to the request,
returning the token to the application.
o
The application is able to continue
(e.g., returning data to the user or allowing access to the application).
All you need to implement this
scenario is a federation service, such as Active Directory Federation Services
(AD FS) 2.0, IBM Tivoli Federated Identity Manager, or Ping IdentityÕs
PingFederate, and a claims-aware application such as Microsoft SharePoint 2010.
In the second scenario, which
Figure 4 shows, the user is inside the enterprise and needs to access an
external web-service provider. There are two major use cases for this scenario.
The first use case is accessing an SaaS provider, in which an enterprise uses a
service such as Salesforce, Google Apps, or a hosted email provider without
maintaining separate passwords at every provider. The second use case is for
B2B collaboration, in which users in the identity providerÕs enterprise need to
seamlessly collaborate with users in another enterprise who have documents to
share. In this case, the claims-aware application might be SharePoint, which
would let users from both enterprises post and work with documents. This
overall scenario is broadly known as Internet single sign-on (SSO). Note that
in this scenario, the user isnÕt actively doing anything, and no applications
on the local computer are aware of the web service; the userÕs browser is
simply redirecting all the traffic through it. This is whatÕs known as a
passive client.
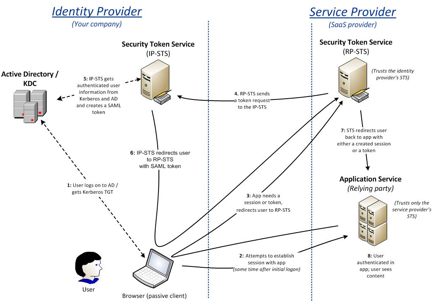
fig 4: internal user accessing an
external application
The single largest difference
between this scenario and the previous one is that the service provider has its
own STS, and the application service trusts it alone. The federated trust
agreements that the service provider establishes with its customers are
supported by the STS, rather than the application service. This service
provider configuration is more scalable than one without an STS because the
resource load of potentially thousands of trusts is focused on the STS instead
of the application service and wonÕt affect the application serviceÕs
resources. ItÕs also more secure, because the application service doesnÕt trust
any external claims—only the claims generated by its own STS.
The passive client and the addition
of the service provider STS add several steps to the process. Instead of the
client actively participating in the authentication process, the application
service redirects the request through the clientÕs browser to the service
providerÕs STS to discover the needed claims (step 3). Then, the service
providerÕs STS sends a token request to the identity providerÕs STS (step 4).
After the identity providerÕs STS generates an SAML token, it redirects the
token through the userÕs browser (neither the user nor the browser has any idea
whatÕs going on) to the service providerÕs STS. This STS will verify it,
generate a token with its own signature (the only one the application trusts),
and present it to the application service (step 7). The process then completes
as expected, and the user is redirected to the application to successfully use
it. For more information about claims-based authentication in SharePoint 2010,
see SharePointPro Connections, ŌUnderstanding Claims
Based Authentication in SharePoint 2010Ķ, as
well as Steve PlankÕs whiteboard video presentation ŌHow ADFS and the Microsoft Federation Gateway work together up in the
Office 365 CloudĶ.
Note that the service provider
isnÕt required to have an STS of its own; the application can directly trust
the identity provider. However, this situation might be more common in the B2B
collaboration use case, where scalability isnÕt an issue.
Federation also works if the user
in the second scenario is outside the enterprise (e.g., working from home on a
nonwork computer without a VPN). Because the user is outside the Kerberos
domain, the employerÕs STS puts up a forms-based authentication page for the
user to directly enter enterprise credentials for authentication. After the
user is authenticated, the claims-based authentication sequence continues.
How Federated Identity Is Used
Now that youÕve seen how some of
federationÕs moving parts work, you might wonder whether anyone has gone to the
trouble to implement it. The adoption of federation technology was slow in its
early years because few companies saw the ROI for internal applications and the
occasional external collaboration. It took cloud computing, an increase in the
number of claims-aware applications, and the explosion of SaaS providers to
really give federation the boost it needed. YouÕre already using it today;
youÕre just not aware of it. (Which, after all, is what federation is all
about; if itÕs doing its job, you shouldnÕt notice it.) If you use any web
services that require Windows Live ID, such as TechNet, MSDN, Windows Live
Messenger, or any of the other Windows Live properties, youÕre already using
federated identity in the consumer space.
Many companies are implementing
federation to keep pace with their usersÕ demands to use SaaS services in a
secure and scalable manner. If you set up a federated trust with the provider,
your users can log on to the service using their own user IDs and
passwords—they donÕt have to create and manage a separate account; itÕs
handled automatically. The enterpriseÕs account management team no longer has
to worry about managing duplicate accounts for multiple SaaS
providers—especially the important security task of deprovisioning
accounts that shouldnÕt be active. And after you set up your federation
environment with your own STS, itÕs a trivial task to add new trusts as you
acquire new service providers and applications.
Who are the major vendors in
federation and Internet SSO software? Microsoft is certainly one of them. AD FS 2.0 is a free
download for Windows Server 2008 R2 or Server 2008. It does a
good job, but itÕs not a trivial implementation; youÕll want to work through
the TechNet documentation
and step-by-step guides in a lab environment
first. Along with AD FS, Oracle Identity Federation, CA Federation Manager, and
Ping IdentityÕs PingFederate comprise the majority of the enterprise Internet
SSO market.
ThereÕs another class of federation
software that sidesteps the need for a local STS installation. Products such as
Ping IdentityÕs PingConnect, Symplified, and Okta make federation itself a
cloud service. The companies host federation software and manage trusts with a
vast number of SaaS vendors so that subscribers to these services automatically
have secure access to the vendors.
A fairly small percentage of SaaS
vendors accept federation today, but the number is rapidly growing. As
federated identity becomes common between enterprises and cloud service
vendors, the idea of using claims-based identity for applications inside your
company wonÕt seem nearly as radical as it does today. A benefit of
claims-aware applications is that they can coexist peacefully with your
existing Kerberos-based infrastructure and applications because the STS
translates the Kerberos identity information into claims for the applications.
Think of the STS as a proxy or gateway between the Kerberos world and the
claims world.
The growth of the market for
internal claims-aware applications (enabling traditional applications and
creating new ones) is a chicken-and-egg situation. ISVs donÕt want to invest in
making applications claims-aware until thereÕs a good customer demand for such
applications. But customers wonÕt generate much demand until theyÕre equipped
to support these applications with a federation service and can use this form
of authentication with little added expense. What will tip the market into
broad adoption is the SaaS scenario that I discussed; companies that add
federation capability to support their SaaS vendors are positioned to begin
using claims-aware applications internally. To help drive this cycle, you
should insist that your SaaS vendors provide federation capability. It reduces
the risk for you, increases your visibility into the cloud, reduces the
vendorÕs need to maintain an identity store, and helps to position your
business to handle claims-aware applications.
Your Next Step with Federated
Identity
The best way for you to get started
in understanding federated identity is to start playing with it yourself. Set
up a federation service in your lab. (IÕll write about my experience installing
AD FS 2.0 in my own lab in my June Enterprise Identity column.) Start the
project to add a federation service for your company. Approach your companyÕs
Information Security team first to gain support; if your security
administrators arenÕt already aware of the risk posed by having separate
accounts for every SaaS vendor, you should make them aware. A federation
service will lower your companyÕs security exposure by decreasing the number of
duplicate accounts with SaaS vendors, decreasing overhead costs if IT is
attempting to manage these duplicate accounts, and making life easier for your
users with fewer logons to remember. If you donÕt want to host a federation
service yourself, federation-as-a-service products such as PingConnect,
Symplified, and Okta will outsource it.
Federated identity is a key enabler to integrating cloud
services and on-premises traditional IT services. At the moment, cloud
computingÕs hype outstrips its current use—but donÕt mistake it for only
a fad. Virtualization, the web, and the Internet itself all went through these
cycles, and theyÕre an accepted part of our infrastructure today. ItÕs time to
begin adding federation skills to your career toolset. FederationÕs importance
will only grow in the future, and these skills will be crucial to both your
company and your career.
http://windowsitpro.com/active-directory/ease-cloud-security-concerns-federated-identity